Endpoint Security Management
How do you eliminate security threats?
Do you protect the endpoints in your organization?
Do you control the use of USB ports on workstations?
How do you protect data from premeditated or careless transfer to portable devices?
Today's IT environments are complex, with almost endless combinations of hardware, software, applications, operating systems tailored to the needs of consumers. Adding to the complexity of verifying and proving compliance with legal regulations and corporate requirements for protecting information resources and supporting mobile users, the need for a comprehensive management solution is obvious. The proposed solution manages and assures the security of all types of devices for different platforms, both in the corporate network on the site and outside of the office.
What do you need?
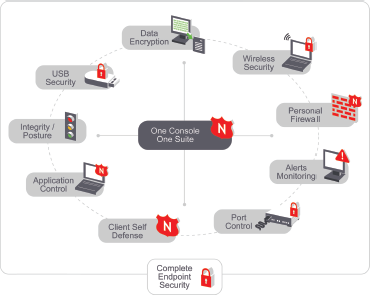
-
Endpoint management solution that provides control over applications, protocols, and removable data devices, provides encryption of files and folders, control over network access, providing current levels of protection.
-
An extensive set of policy-based solutions that protect endpoint devices, including Windows workstations, laptops, tablets, smartphones, MP3 players and other portable devices.
What solution we offer:
Whether you are interested in identifying theft, fraud or other internal threats, or you meet legal requirements, the number of threats to your network increases each year. Although there is no way to completely eliminate all security threats, we can help you identify and recover vulnerabilities as soon as they are discovered.
If you want:
-
to control the use of workstation USB ports, protect data from premeditated or careless transfer to portable devices, disable the use of flash drives, CD / DVD writers and other types of portable media,
-
or allow read-only mode on them, perform precise serial number control, encrypt files stored on portable devices, control and manage wireless network connections,
-
build a personalized, easy to use Firewall to protect from hackers, malware, protocol attacks, etc., to control applications,
You need a solution that will provide complete protection for endpoint devices without budget draining or overloading IT staff.
All this based on predefined policies is managed by one console.
We offer an endpoint management system, which contains a wide range of policy-based solutions that protect Windows workstations.
Key Features
-
Personal Firewall - Stable and easy to use, it is a firewall against hackers, malware, protocols attacks, and more. Centralized, policy-based control over firewall settings that cannot be disabled or circumvented by end users or unauthorized administrators.
-
Wireless Security - Provides centralized control over where, when and how users can connect to wireless networks. Wi-Fi management that allows you to create white and black lists for wireless access points and implement policies that restrict, disable or block Wi-Fi communications in specific situations.
-
USB Security - Data theft protection that allows you to enable, disable or set any removable file storage device to read-only—including USB, floppy, CD/DVD and zip drives; .mp3 players; and flash memory, SCSI and PCMCIA cards.
-
Application Control - Gives precise, policy-based control over the applications running on all your endpoints. Location-based application control that can allow specific applications to run, deny them access to the network or prevent them from running altogether—all based on the security of a user’s location
-
Port Control – Complete protection for every other type of wired and wireless port and communication device. This includes LAN, USB, 1394 (firewire), serial and parallel ports, as well as modems, Bluetooth and infrared (IrDA) connections.