Employees often have to travel to the offices of their future customers. During negotiating with them, they have to access a sensitive information. If the ways they use to connect to the head office are insecure, malicious programs or people can easily access this data. This would be detrimental at least to the business interests of the organization. For this reason, a secure connection with internal resources is very important and how to build its protection is the main purpose of this solution.
What you need:
- A solution to control access to both web applications and applications inside the organization.
- Reduce the risk of incompatibility with requirements for protection of personal data and other privacy requirements
- Communicate with internal and external business partners
What solution we offer you
To compete successfully, your business needs to be accessible to all types of users, including employees, customers, and partners, regardless of where they are located or daytime. Our proposal solves this challenge by helping you increase user access without compromising security or control.
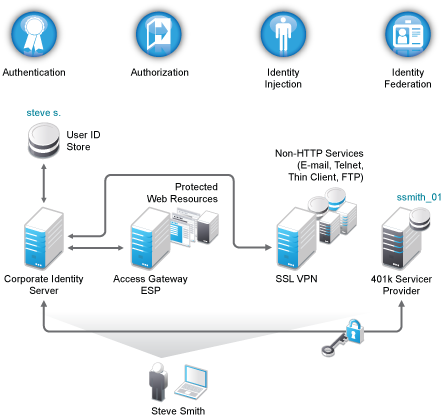
The solution simplifies and guarantees on-line asset allocation, helps control customer access to web-based and traditional business applications. Authorized users are granted authenticated access to portals, web-based products, and corporate applications. IT administrators have access to centralized, policy-based authentication management and access privileges. Furthermore, the solution supports a wide range of platforms and directory services, and is flexible enough to work even in the most complex and various computing environments of different manufacturers. Support for basic identification standards such as SAML, WS-Federation and Liberty Alliance is included.
To help you manage access to vital data in your business, the solution provides:
- Role-based and privileged authentication
- Consecutive implementation of security policies
- Multi-factor authentication, data encryption and SSL VPN
- Web single sign-on
- Reports at customer request
- Ability to create a federation - user of one partner in the federation to reach the resources of another partner in a secure and trusted manner
- Modular functionality
Benefits
- You allow users access to the necessary IT assets outside the firewall
- Sharing identities and privileges for access with trusted partners
- You enable and disable real-time access
- Confirm your commitment to the business in real time
- You are preparing reports for web events and attempts to access
We offer a complete access control solution that provides secure access to Web and corporate applications. It also provides seamless single sign-on, based on industry standards such as Seamless Assertions Markup Language (SAML), WS-Federation, and Liberty Alliance protocols, combining simplified deployment and management with advanced capabilities such as multi-factor authentication, role-based access, Web single sign-on, data encryption, and SSLVPN. It Integrates with Novell eDirectory or Microsoft Active Directory.
Non-functional features
The proposed access control solution has the following non-functional features:
- It can be built, in whole or in part, into a virtual environment that determines the full use of hardware resources and its easy expansion in the future. VMware and XEN virtualization environments are supported.
- The solution is multi-platform, can be built on both Linux and Windows servers. For better price, stability, and protection against malware, INTEPRO recommends deployment on SUSE Linux Enterprise Server.
- The solution is component-based and the number of individual components depends solely on the client's needs for distribution, reservation and fault-tolerance.
- It can be further developed with authentication methods (eg smart cards, tokens, etc.).